What happens if a backdoor to the corporate network is left open? Hackers immediately seize the opportunity, infiltrate, and remain unnoticed in the background until they strike... With Honeypot, this is a thing of the past! The solution ensures that an organization is immediately alerted when hackers infiltrate the network.
Silent Alarm
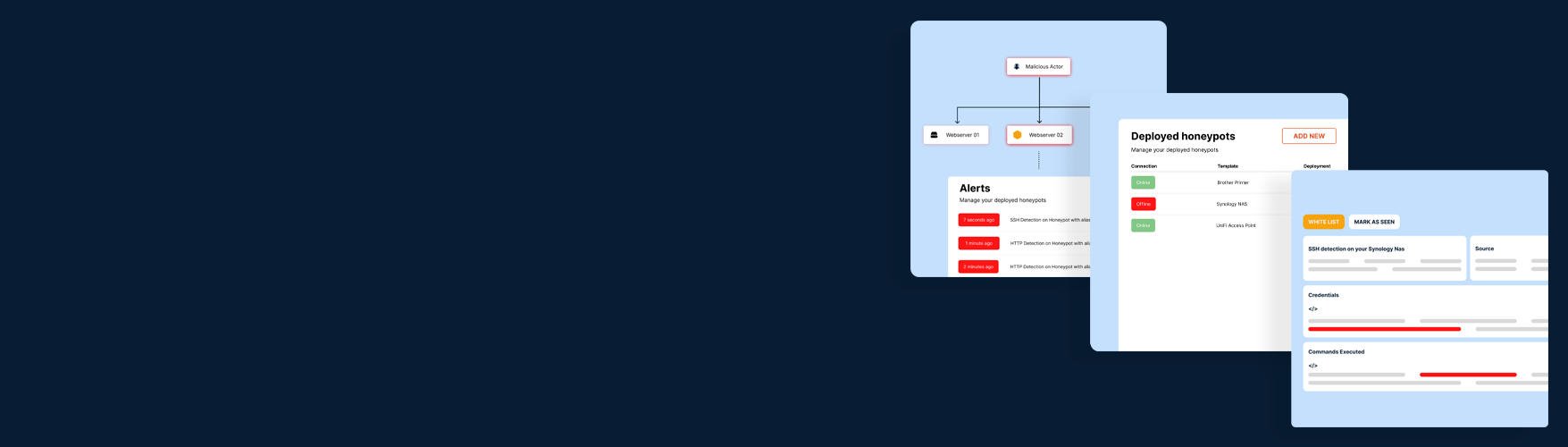
Preventive security is, of course, indispensable, but how does an organization handle it if a hacker manages to penetrate the corporate network? The Network Intrusion Detection System (NIDS) within Honeypot acts as a safety net: With smart sensors, you place a decoy device among other devices in the network - think of a server, storage, or network device. It lures hackers and leads them away from critical systems. The organization receives an immediate notification when such a threat is detected.
Know how to act
With Honeypot, an organization obtains detailed information about the hacker and the attack, so they can act immediately and take the appropriate measures; Block the attacker, strengthen security, and take legal action if necessary. Honeypot increases your customer's network security with the following features:
- Detect & Distract - Honeypot detects hackers and keeps them busy in a controlled environment to waste their time.
- Threat Alert - The IT administrator receives an immediate warning when a threat is detected, allowing immediate action to be taken.
- Fingerprint - Hackers leave traces; track and identify cybercriminals across different attacks and periods.
- Integration with trusted systems - Honeypot integrates with the organization's monitoring system for a complete network overview.
- Recommendations - Honeypot provides practical advice to respond appropriately once a hacker is detected.
- Credentials - The tool collects used credentials during attacks to tighten security measures and policies. Was it a brute-force attack or a malicious act by a former employee?
- Collects evidence - Honeypot collects evidence for insurance, legal action, or filing a report.
- Generates reports - Honeypot exports data in a format accessible to both users and administrators. Export a report or use the SecurityHive API.